Overview
A key part of every SAML communication between Egnyte and IdP is the signature used to sign requests between the two entities. Due to recent security update, the SHA-1 algorithm will no longer be supported as it is considered unsafe. It is recommended to update the chosen algorithm in any IdP setup that use old and unsupported ones to SHA-256.
Instructions for Common IdP Setups
OneLogin
1. Log in to the OneLogin console as an admin and access "Administration" panel on the top right.

2. Go to Applications List and select Egnyte application that the customer is using.

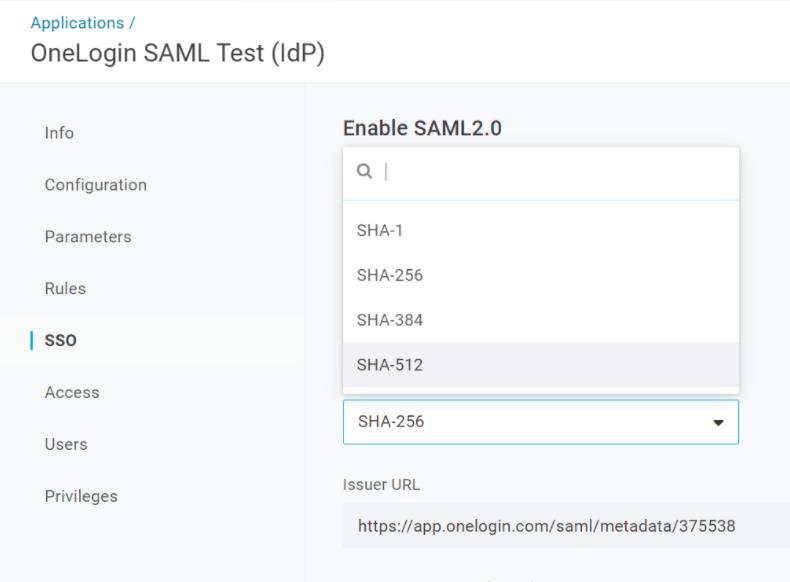
3. In "SSO" panel select SHA-256 from the "SAML Signature Algorithm" dropdown and click "Save" in top right.
Azure
For customers that have not created a new SHA-256 cert previously on Azure SSO:
1. Login to "https://portal.azure.com/" as an admin and access "Azure Active Directory.
2. Go to "Enterprise applications" and select Egnyte application that the customer uses.
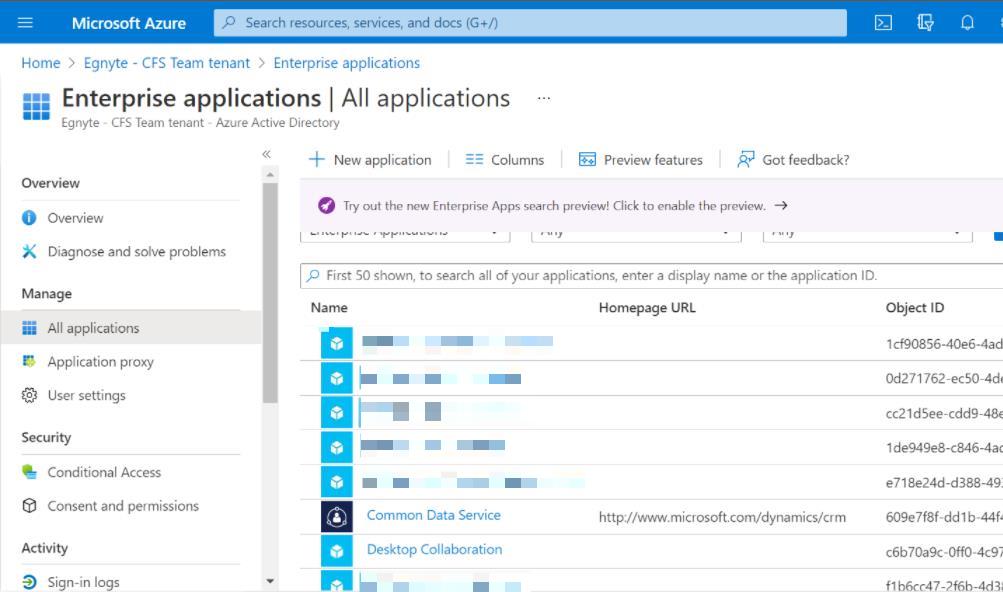
3. In "Single sign-on" locate "SAML Signing Certificate" and click Edit.
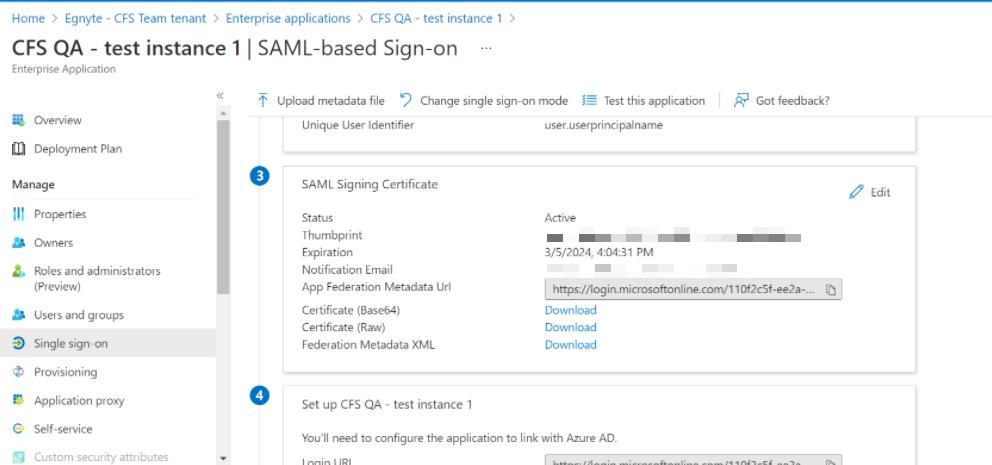
4. Create new cert by clicking ‘ + New Certificate’ (make sure to select SHA-256).
5. Once cert is saved on the list above, ACTIVATE IT and download it.
6. Go to Egnyte, replace existing cert with downloaded one, save.
7. Navigate back to Edit the SAML signing certificate tab on Azure.
8. Change the ‘Signing Option’ from ‘Sign SAML assertion’ to ‘Sign SAML response’ and click Save.
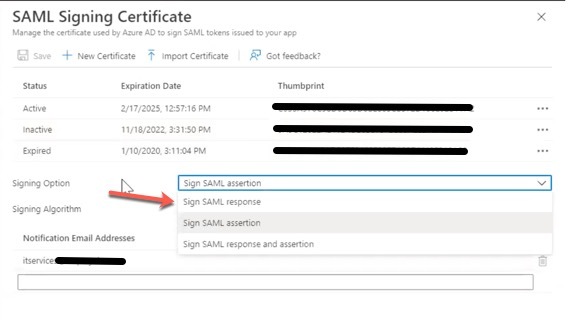
9. Wait for few seconds for the change to apply.
10. Change the ‘Signing Option’ back to ‘Sign SAML assertion’ and click Save.
For customers that have created a SHA-256 cert but still sending SHA-1 on Azure SSO:
1. Navigate to the Single sign-on on the Azure portal.
2. Edit the SAML signing certificate tab.
3. Change the ‘Signing Option’ to ‘Sign SAML response’ and save.
4. Allow a few seconds for the change to apply.

5. Change the ‘Signing Option’ back to ‘Sign SAML assertion’ and save.
Okta
Okta uses predefined Egnyte app that has a hardcoded SHA-256 certificate, so no change is required.
Other Providers
As Egnyte supports every provider that is SAML-compliant, it's hard to provide detailed instructions on each of them separately. However, general rules on how to locate the signing algorithm setting are the following:
1. Log in to IdP as an admin.
2. Go to list of Applications (may also be called connectors/entities/etc) and find one used for Egnyte authentication.
3. In Single Sign-On settings find value that uses "SHA-1" - it may be called "Signature Algorithm", "SAML Signature Value", etc, etc.
4. Update algorithm to SHA-256 and save.
Allow couple minutes for change propagation on IdP side and test login.
Instructions presented in this article are subject to change based on the IdP service provider. Refer to your IdP service provider's own documentation for more accurate information.